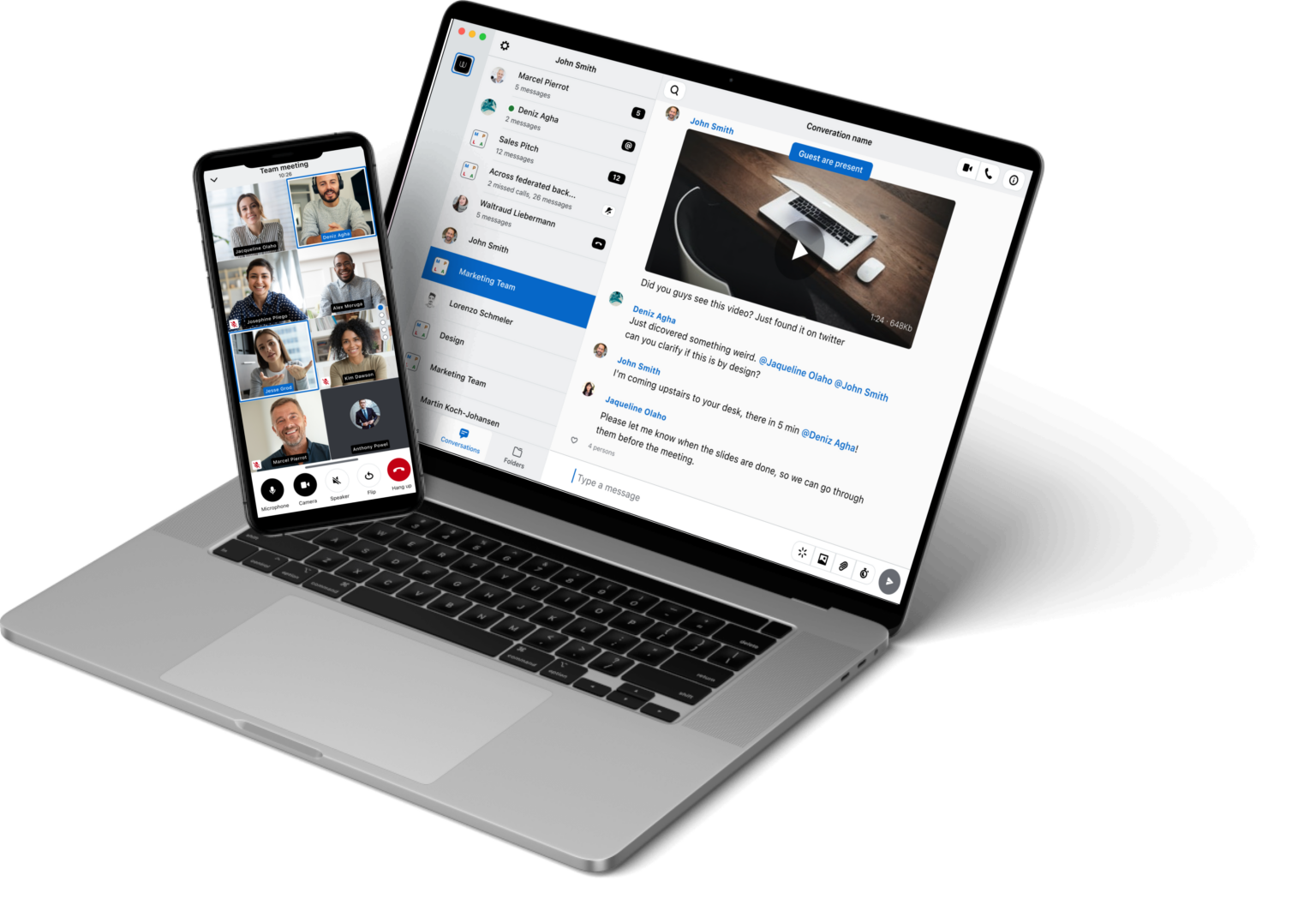
Improved Usability: Wire's Desktop & Web Updates
Discover Wire's latest updates, including an improved calling UI, enhanced conversation views, read receipts, and more.
Simply the most Secure Messenger


Discover Wire's latest updates, including an improved calling UI, enhanced conversation views, read receipts, and more.

Wire and Schwarz Group announcing a strategic partnership and investment to strengthen the digital infrastructure of Europe.

New allegations show why Meta apps like WhatsApp should not be used in professional circumstances.

Wires new CEO Benjamin Schilz sits down to answer questions about his vision for Wire, lessons from companies he founded and why...

The Taurus' leaks have shaken politics and society in Germany. We are taking a closer look on what to look for in a secure...

Picking the right Wire deployment for your organization might be tricky. In this blogpost, we are breaking down the options to...


Interview with Robert Kallwies Wires' new director for information security. Robert explains his take on security and his...

A brand new standard for end-to-end encrypted messaging, federated secure messaging and a new Android app. Only some news from...

Wire joins a coalition of global industry leaders to push for open standards and innovation in technology.