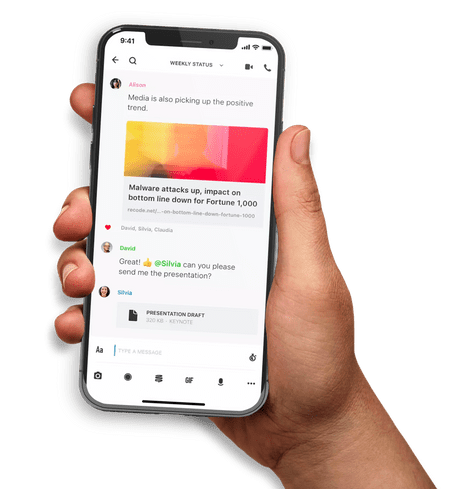
The platform for confidential communication
On Premises or in the Cloud - simply secure! With Wire, you communicate at the cutting edge of technology thanks to Wire Federation and MLS.
Uncompromising Security
Secure messaging for large groups that comes from one of the initiators of the MLS standard and is ready for post-quantum security and interoperability
Communicate Across all Devices
Wire is available on iOS, Android, macOS and Windows as well as in your browser – so you stay productive on all your devices
End-to-End Encryption
Industry-leading, end-to-end encryption that’s always activated to protect your conversations, calls and shared documents
Wire Cloud
Our cloud service combines the highest security standards with maximum flexibility, connectivity and usability. Communicate securely with coworkers, customers and business partners using always-on, end-to-end encryption. Works across all operating systems on up to 8 devices per user account.

Wire On-Premises
For customers with particularly stringent requirements for data sovereignty. It offers the highest level of security and control and can be managed by Wire specialists if required. The federation option also enables you to share information securely with external business partners
Quick Facts:
The Wire Messenger offers a unique combination of maximum security, usability and data protection. Full transparency and data sovereignty included.
Confidential Communication – Complies with VS-NfD Standards
- Wire has a security clearance for VS-NfD content (“classified information – for official use only” category in Germany)
- Used by public authorities that regularly communicate classified information
Wire Federation
- Enables communication across multiple on-premises instances
- The interconnection of multiple instances can comply with your specific security regulations (Not Fully Connected graphs)
- Coming soon: On-premises instances can federate with Wire Cloud
Secure Communication for Regulated Companies
- The Wire Legal Hold function enables you to securely archive conversations with always-on, end-to-end encryption
- Allows you to meet compliance regulations, such as those in the finance industry
- Avoids the risk of large fines for using unauthorized communication tools
- Offers proven Wire security
Messaging Layer Security (MLS)
- Wire is one of the initiators behind the Messaging Layer Security protocol – the future-oriented standard for secure communication
- High-performance communication, even in groups with several hundred participants
- Ready for post-quantum security
- Basis for the interoperability between different messengers as required by the EU
- Available from 2024
Innovative Security Benefits
Wire provides market-leading security for messaging as well as for audio and video communication. Our security experts implement the current state of research in Wire and are active in helping to shape international security standards, such as Messaging Layer Security, to ensure the best possible security level.
Consistently Open Source
We are committed to open standards and open-source code. This ensures that our security claims can be verified by external specialists at any time. You can find more information about our open-source approach on Github.
Deployment
Wire Cloud
Our cloud service combines the highest security standards with maximum flexibility, connectivity and usability. Communicate securely with coworkers, customers and business partners using always-on, end-to-end encryption. Works across all operating systems on up to 8 devices per user account.Benefits
- Maximum connectivity
- Easy deployment
- Easy team management
- Operator and administrator shielding
- Hosted in the EU
Wire On-Premises
For customers with particularly stringent requirements for data sovereignty and security. It offers the highest level of security and control and can be managed by Wire specialists if required. The federation option also enables you to share information with external business partners.
Benefits
- Maximum security and sovereignty
- Tailored to your infrastructure
- Full control over your data
- Includes all functions in the cloud solution
CONTACT
Learn More About the Wire Messenger
Wire Messenger combines security, privacy and ease of use in the best way. Extensively tested and approved by the most demanding companies worldwide.
Fill out the contact form and we will get in touch with you. We will be happy to answer all your questions and requests.