The Digital Operational Resilience Act (DORA) reshapes the European regulatory landscape by mandating financial entities to treat digital resilience as seriously as credit or liquidity risks. For companies navigating digital transformation, understanding DORA's five foundational pillars is critical to ensuring secure internal communication, business continuity, and regulatory compliance.
Explore how Wire helps financial institutions meet DORA standards with secure, compliant communication tools. To help companies navigate the complexity, Wire partnered with Reuschlaw to develop a new whitepaper that breaks it all down.
Read more ->
What is DORA?
The Digital Operational Resilience Act, commonly known as “DORA”, is a regulation adopted by the European Union (EU) to harmonize and strengthen the digital operational resilience of the financial sector. Officially titled Regulation (EU) 2022/2554, DORA came into force in January 2023 and became fully applicable as of 17 January 2025.
What makes DORA unique is its technology-neutral approach combined with legal enforceability across all EU member states. Because it is a regulation (not a directive), DORA is directly applicable without the need for national transposition, ensuring consistency and immediacy in its enforcement.
But knowing the regulation is just the first step.
In our latest article, we take a closer look at two critical challenges that make DORA compliance especially complex, and how organizations can address them before they become risks.
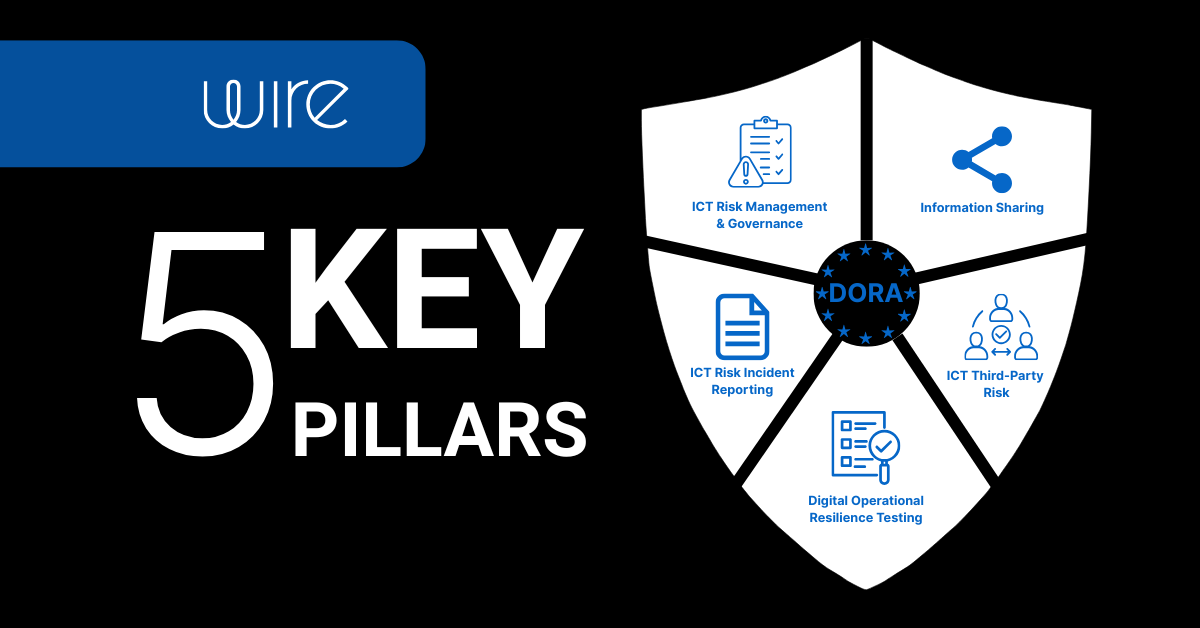
What Are the Five Pillars of DORA?
1) ICT Risk Management
What it requires:
Every financial entity must establish an internal governance framework to manage ICT risks.
This includes mapping digital assets, classifying risks, and designing business continuity and disaster recovery plans.
Key actions:
- Define critical business services and their ICT dependencies
- Maintain an up-to-date inventory of all ICT assets
- Implement access control, patching protocols, and change management processes
- Embed cybersecurity awareness across all departments
2) Incident Reporting & Management
What it requires:
Entities must classify, record, and report major ICT-related incidents, and optionally notify significant cyber threats.
Reporting framework:
- Notify senior management and competent authorities of all major ICT-related incidents
- Report incidents using harmonized templates, with thresholds and timelines defined by the European Supervisory Authorities (ESAs)
- Maintain audit trails and communication logs
- Inform clients without undue delay if a major ICT-related incident has an impact on their financial interests
3) Digital Resilience Testing
What it requires:
Organizations must regularly test their ability to prevent, detect, respond to, and recover from ICT disruptions.
Testing regime includes:
- Annual vulnerability assessments
- Live threat-led penetration testing (TLPT) every three years for entities deemed significant
- Red teaming, stress tests, and simulations
- Independent verification and documentation of testing outcomes
4) Third-Party Risk Oversight
What it requires:
Financial institutions must map all ICT providers, assess risk concentration, and embed contractual safeguards for oversight.
DORA mandates:
- Minimum requirements for outsourcing agreements (e.g., data location, access controls)
- Continuous monitoring of outsourced functions
- Contingency planning and exit strategies
- Clear roles and accountability retained by the financial entity, even when services are outsourced
5) Cyber Threat Intelligence Sharing
What it requires:
While not mandatory, financial entities are strongly encouraged to participate in cyber threat information-sharing arrangements.
Expected practices:
- Join sectoral or national Information Sharing and Analysis Centers (ISACs)
- Conclude formal cyber threat exchange agreements
- Notify regulators of participation in sharing ecosystems
- Use findings to update internal risk and response frameworks
Get Ahead of the Curve with Wire
At Wire, we help regulated organizations meet the communication demands of DORA—with secure, resilient, and compliant internal collaboration tools that keep your teams connected, even during crises.
- Encrypted fallback communication for incident response
- Support for crisis simulations
Ready to make your comms DORA-compliant?