Securing High-Sensitivity Workflows
Wire keeps sensitive conversations private with end-to-end encryption and zero-knowledge architecture, protecting messages, calls, and files across teams.

The Costly Threat Environment
Most messaging platforms aren’t built for sensitive communication. With data breaches averaging $4.9 million and 72 percent of messaging apps sharing user data with third parties or storing it in environments accessible to operators or attackers, everyday communication becomes a serious risk. For organizations handling proprietary data, strategic decisions, or public-sector information, these weaknesses significantly increase exposure.
Why Organizations Need Secure Confidential Communication for High-Sensitivity Work
Everyday tools expose sensitive data through external storage, admin access, or insecure infrastructure.
- R&D teams share proprietary data, models, and intellectual property
- M&A and strategy teams exchange confidential documents and early-stage plans
- Finance teams handle forecasts, earnings, and investor-sensitive information
- Legal teams and leadership manage privileged and high-risk decisions
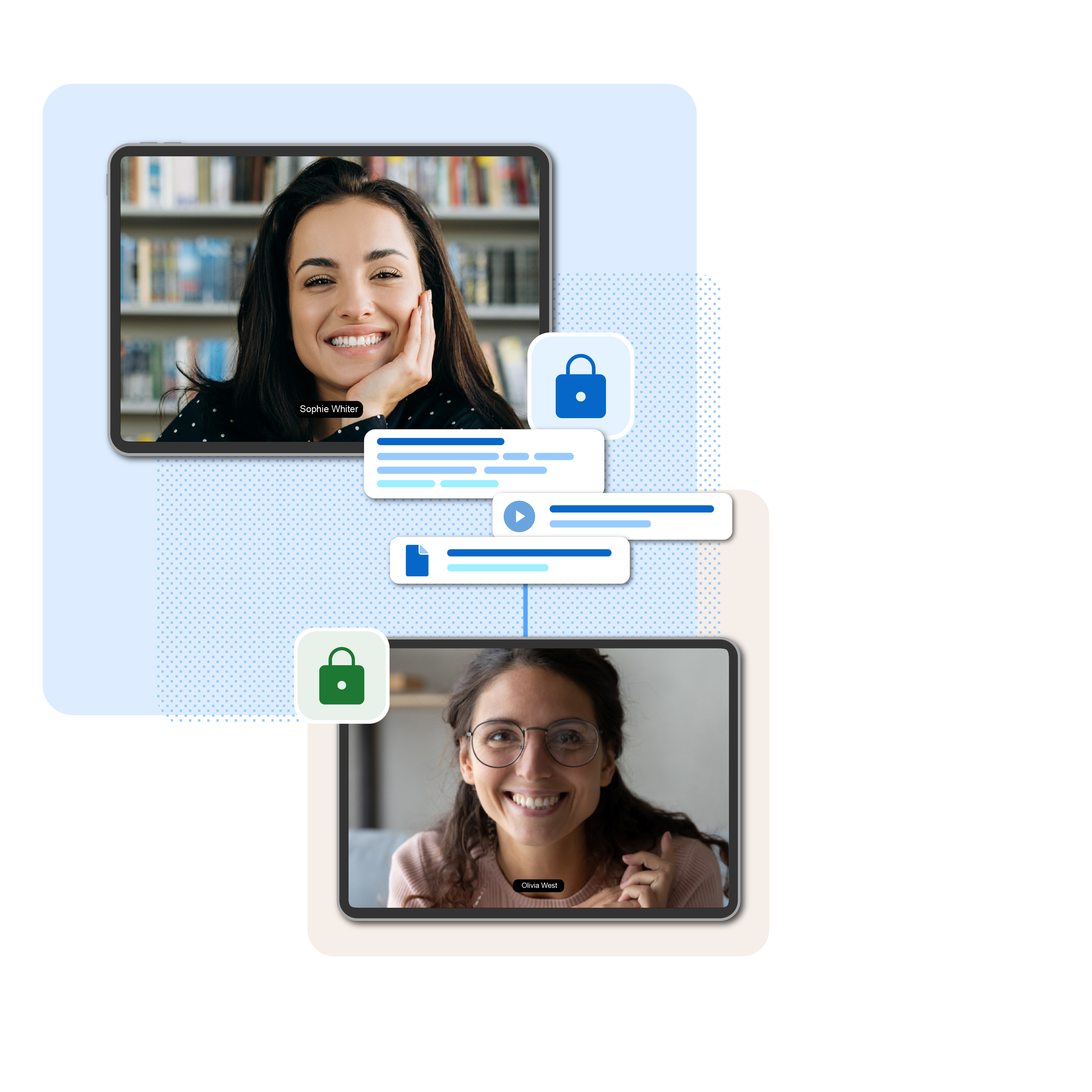
What Effective Confidential Communication Requires
A collaboration platform designed to bring the highest level of security, scalable and configurable to even the most complex organizational structures.
- End-to-end encrypted communication for messages, calls, and files—no server or admin access
- Zero-trust collaboration with verified identities and controlled access across devices
- Secure file sharing and collaboration for sensitive documents, including previews and access control
- Compliance-ready by design, meeting GDPR, NIS2, DORA, and industry standards
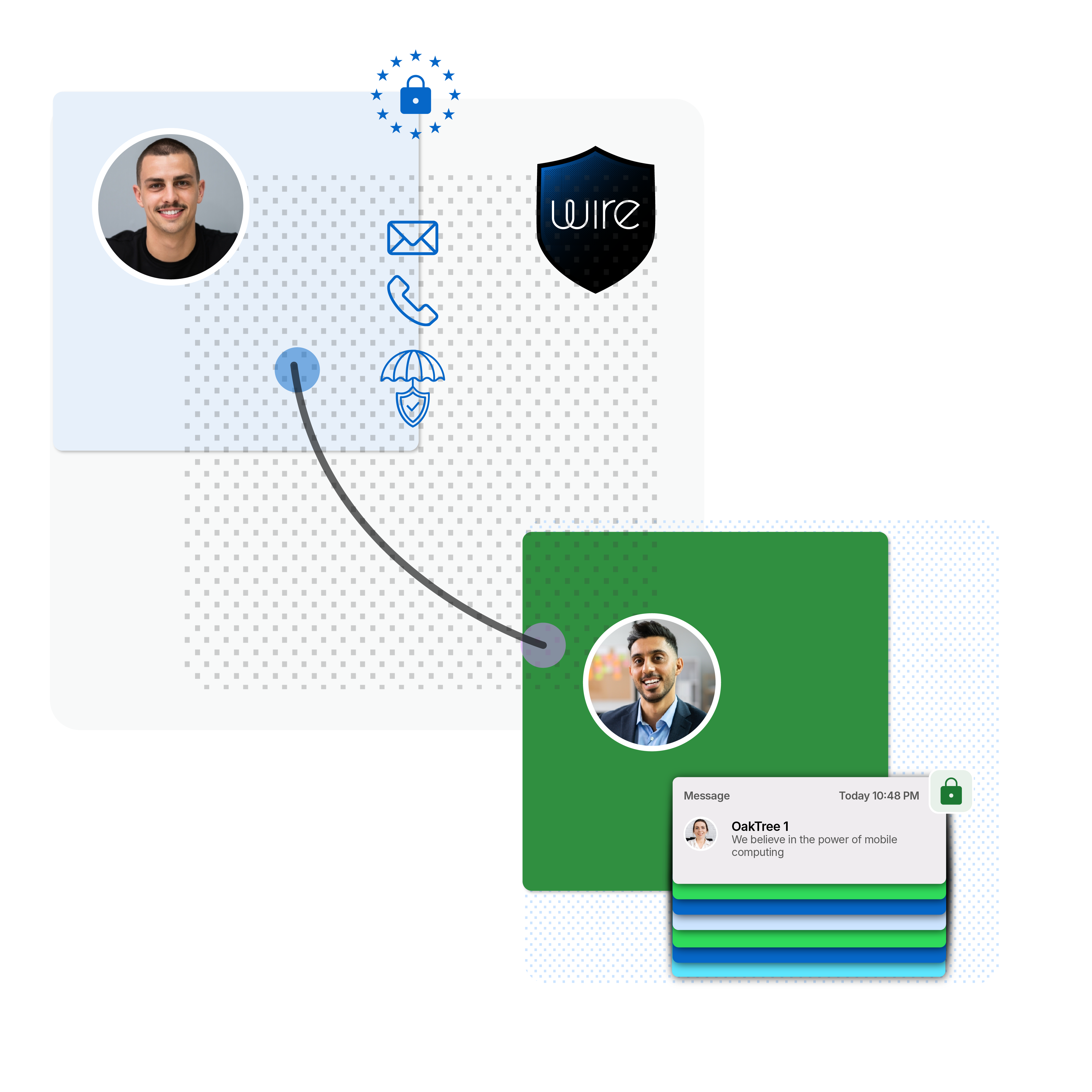
Wire - Built for High-Value and Confidential Communication
Wire is Private by design and Secure by default. No administrator, cloud operator, or third party can access your content.
Key Capabilities
- Zero-knowledge architecture - Even Wire administrators cannot see message content.
- Digital sovereignty - EU-hosted infrastructure supports strict privacy, compliance, and data residency needs.
- User-based access control - User-controlled group settings and privacy, admins don’t control who has access to information
- Available across devices - Wire works on iOS, Android, desktop, and browser (up to 8 devices per user).
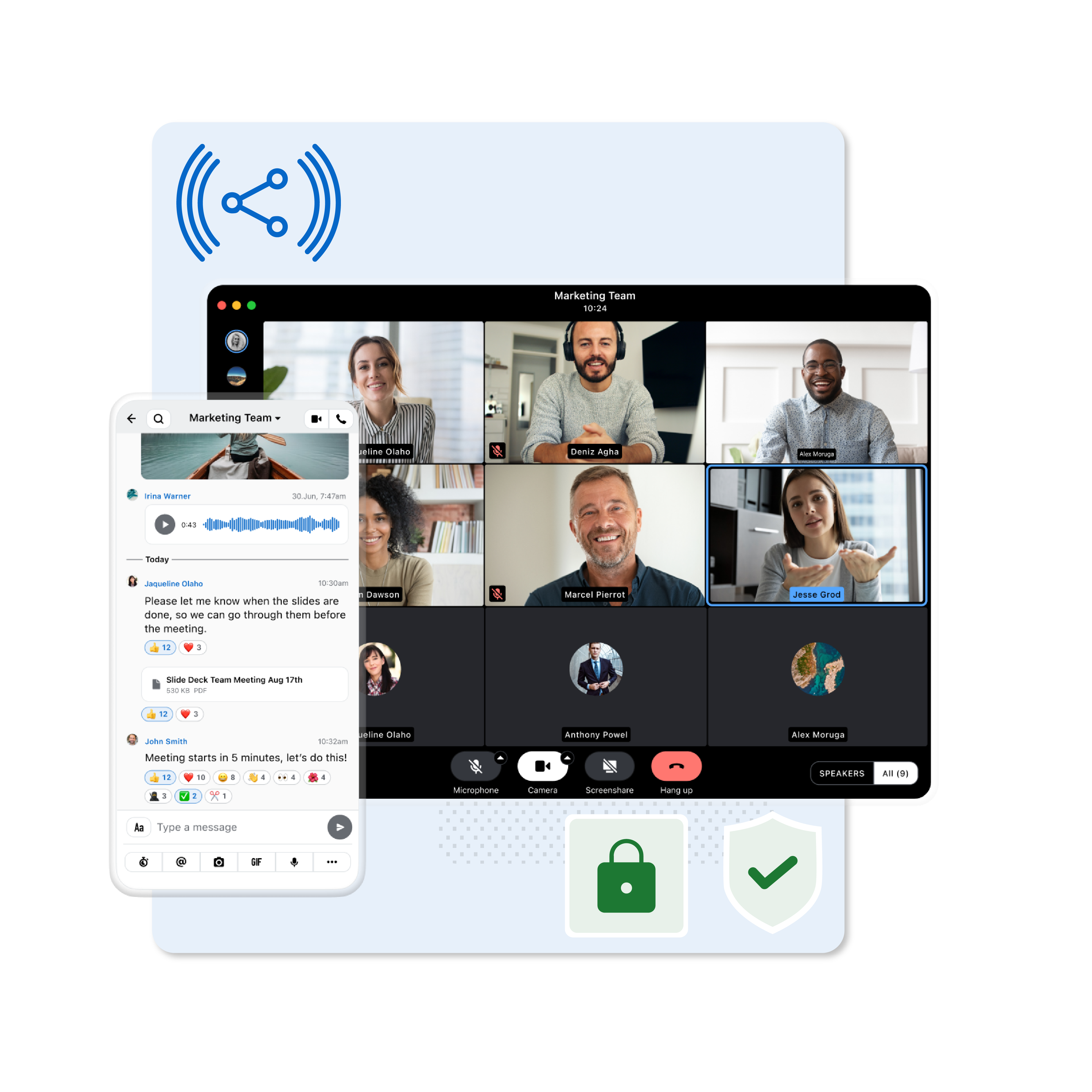
Wire in action
Discover why 1,800+ global organizations trust Wire
Important features for secure communication

Always-on end-to-end encryption
Every interaction is encrypted to maintain confidentiality during a breach, ensuring that all communications are secure.

ID Shield for trusted device verification
Automatically verify and manage device access through trusted Identity Providers, ensuring that only authorized devices participate.

Secure file sharing
Share investigation findings, logs, and recovery plans securely, without relying on compromised primary networks.

Admin & Operator shielding
Administrators are unable to access user conversations, ensuring that even if an admin account is compromised, your communication remains protected.
Communicate with Confidence
Your most important conversations require more than convenience. They require privacy, control, and a secure communication platform. Wire protects sensitive information with modern, scalable security made simple.





.svg.png?width=500&name=BMW_logo_(gray).svg.png)
