Secure, easy identity verification for trusted collaboration
Protect your team from impersonators or unauthorized access. ID Shield lets you easily verify your employees and their devices.
Defending against impersonators, hackers, unauthorized access
- Criminals always find new ways to access systems. You need a simple way to protect your organization when an account is compromised.
- Current tools can't verify users or use cumbersome, manual processes that result in users dropping off.
- It’s not a matter of if, but when. Do you have a plan for how you can recover post-compromise?

Reduce risks - keep your team protected even during a breach
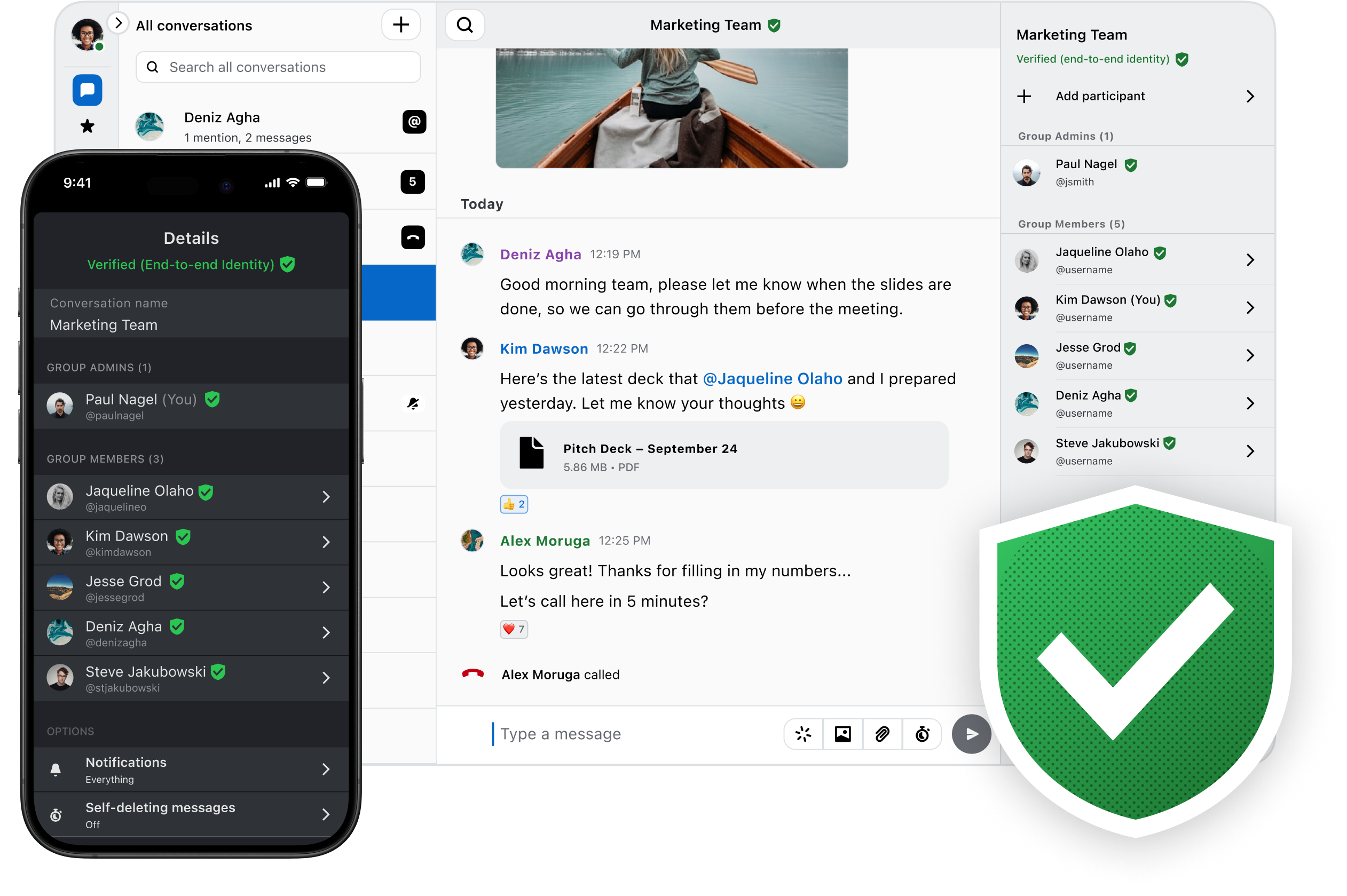
- Easily verify participants and their devices, ensuring that scammers and deepfakes can't impersonate team members.
- ID Shield's automated and transparent certification status indicator makes it simple to ensure that only authorized users are participating in a conversation.
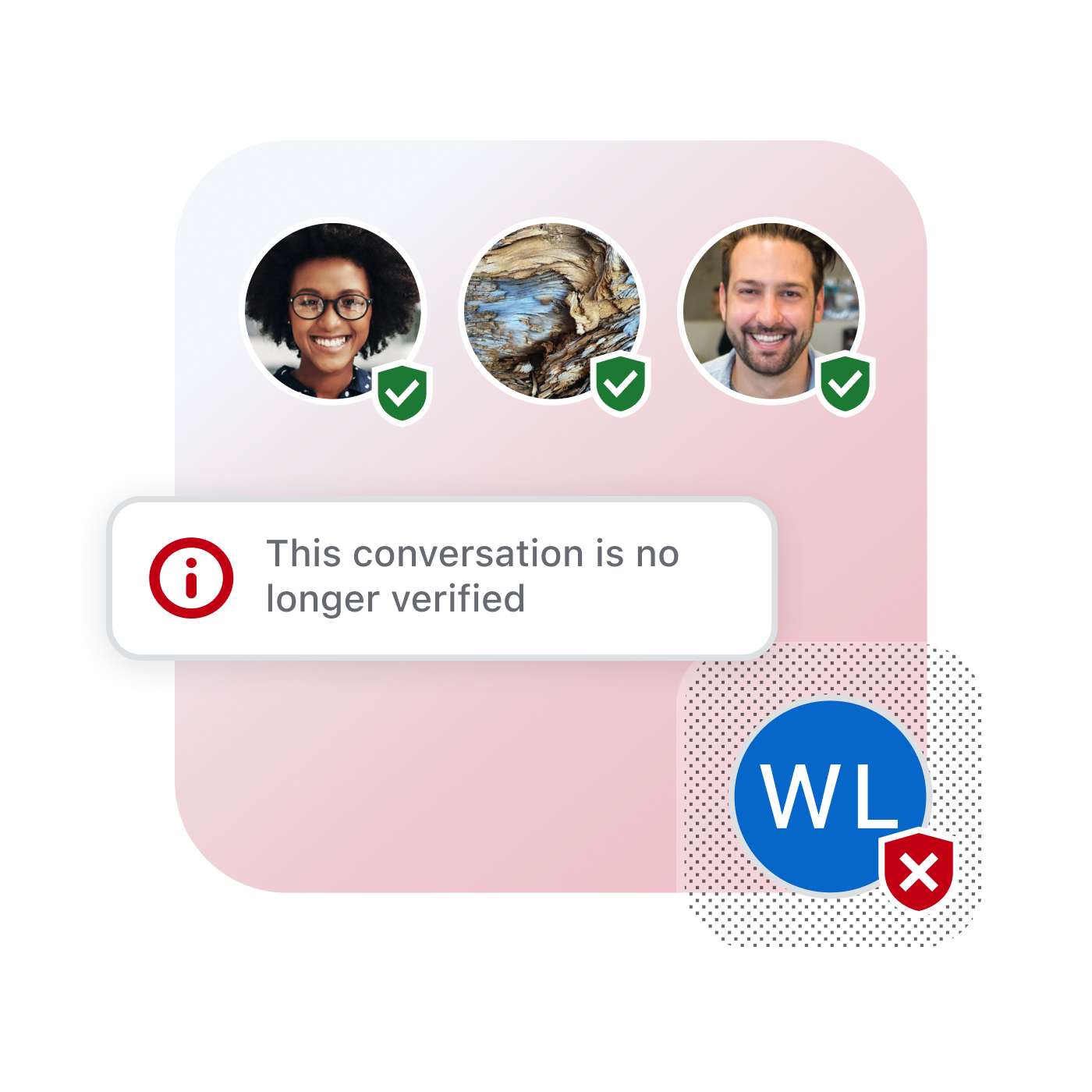
- In the event of a compromised account or data breach, team admins can immediate revoke and quarantine an account. Keep the exposure limited, without disrupting your team's daily operations.
Manage and authenticate, renew, and revoke
- Enroll and renew your team members' devices through your Wire backend. Use a special certificate process and your organizations Identity Provider. Verify people and their devices, including usernames and profile names. Remove members from Wire if they don’t enroll.
- Extend or cross-sign the verified status among different, trusted backends. For example, device A is verified by backend A, which can share that status with backend B.
- In the case of a compromised device or account, you can revoke a certificate. All other devices won’t trust the specific device or account.
What is ID Shield?
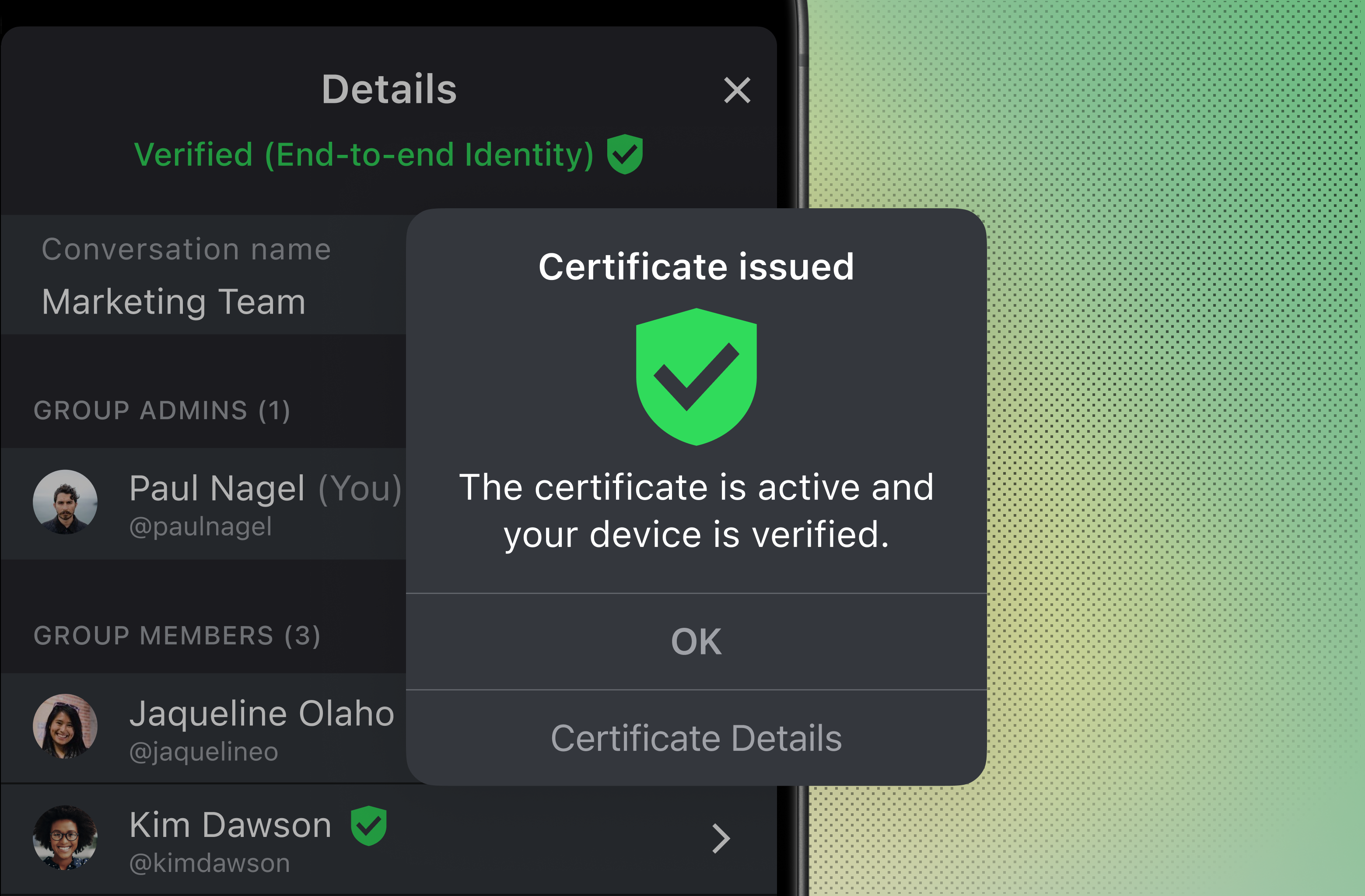
ID Shield makes Wire’s usage more secure and practicable. The device verification takes place automatically using a certificate and replaces the previous manual process by comparing key fingerprints. This way, you communicate with the highest security standard.
ID Shields based on the usage of Messaging Layer Security (MLS)
What does “verification” mean for the final user?
If all user devices are verified, then this person will be shown as verified and also visible to other participants. This helps you to know you are communicating with the right person and ensures a higher security standard.
Is ID Shield available on Wire cloud?
No ID Shield isn't available on the Wire public cloud. ID Shield is only available on on-premises deployments and Wire private cloud.
What happens when a device is compromised?
When a device is compromised, the certificate of that device is revoked. Meaning that all other devices will no longer trust that device once they become aware of the revocation.