Big Tech is Making Data Sovereignty Promises it Can’t Keep
US surveillance laws override EU privacy rules, why Microsoft and other tech giants can't keep their promises on data sovereignty, and what the EU...
Author:

US surveillance laws override EU privacy rules, why Microsoft and other tech giants can't keep their promises on data sovereignty, and what the EU...

Recent findings show that between September 2024 and early June 2025, Meta’s Android apps (Facebook and Instagram) covertly tracked users’ web...

Is Telegram secure or a surveillance tool in disguise? Investigative reports reveal ties to Russian intelligence and major privacy flaws. Learn what...

Discover five key lessons for IT and cybersecurity leaders after SignalGate: from risks of consumer apps to why UX and admin controls matter in...

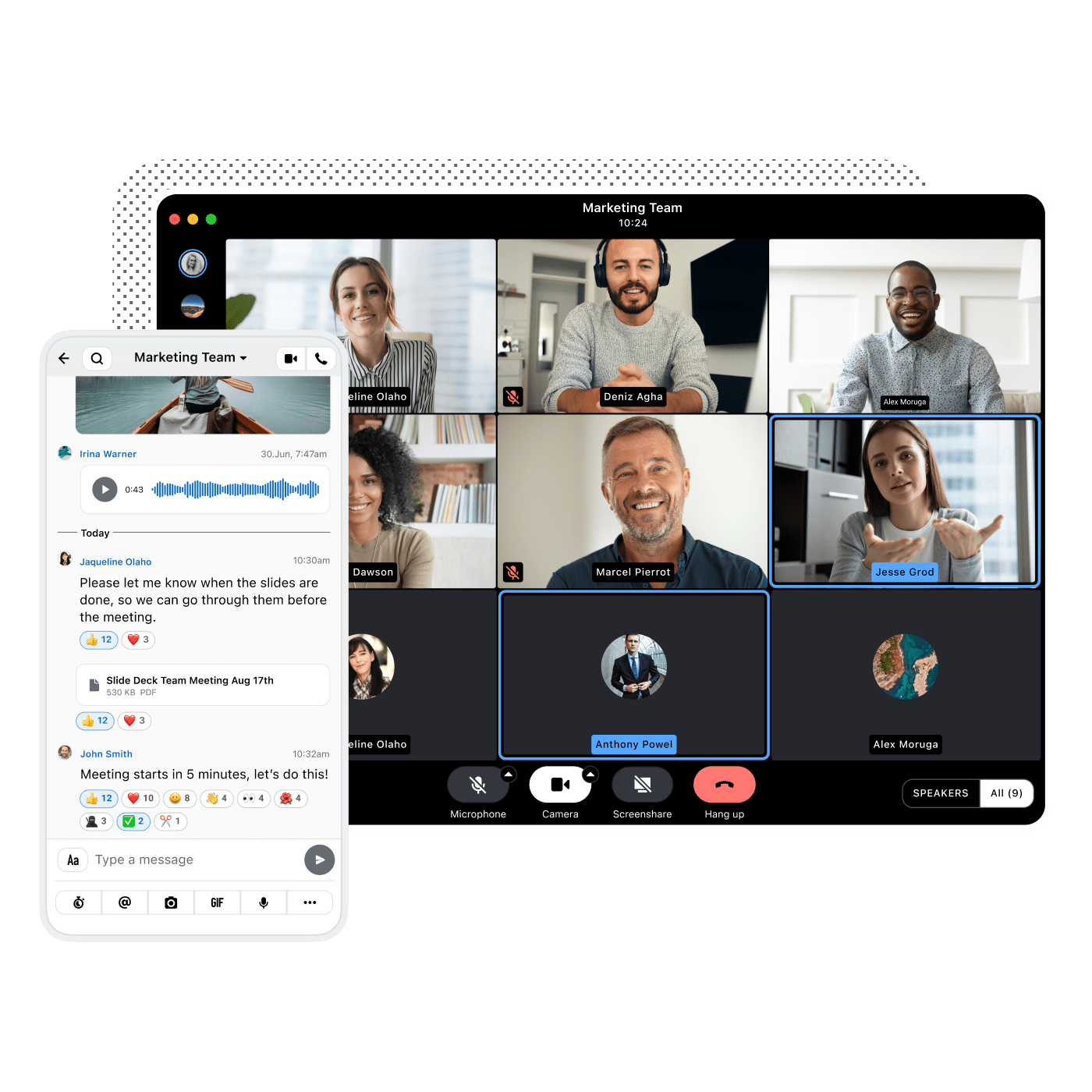
Is your team at risk of corporate espionage or data leaks on Slack? Discover how cybercriminals exploit messaging platforms and what you can do to...

EU organizations face heightened data privacy risks as the EU-US Data Privacy Framework weakens. Discover why secure, end-to-end encrypted...

Learn why end-to-end encryption and zero-trust architecture are essential for secure enterprise communications in the wake of the China Salt Typhoon...

WhatsApp’s Phone Number Dependency Problem

Powerful insights and key take-aways

Discover in a quick call how Wire enables secure, compliant, and seamless collaboration for your organization, without compromising on usability or control.