Digital Sovereignty in Action: Wire Hosts European Leaders in Brussels
Discover key insights from Wire’s Brussels event on digital sovereignty, NIS2 compliance and secure European communication. Learn how Europe is...
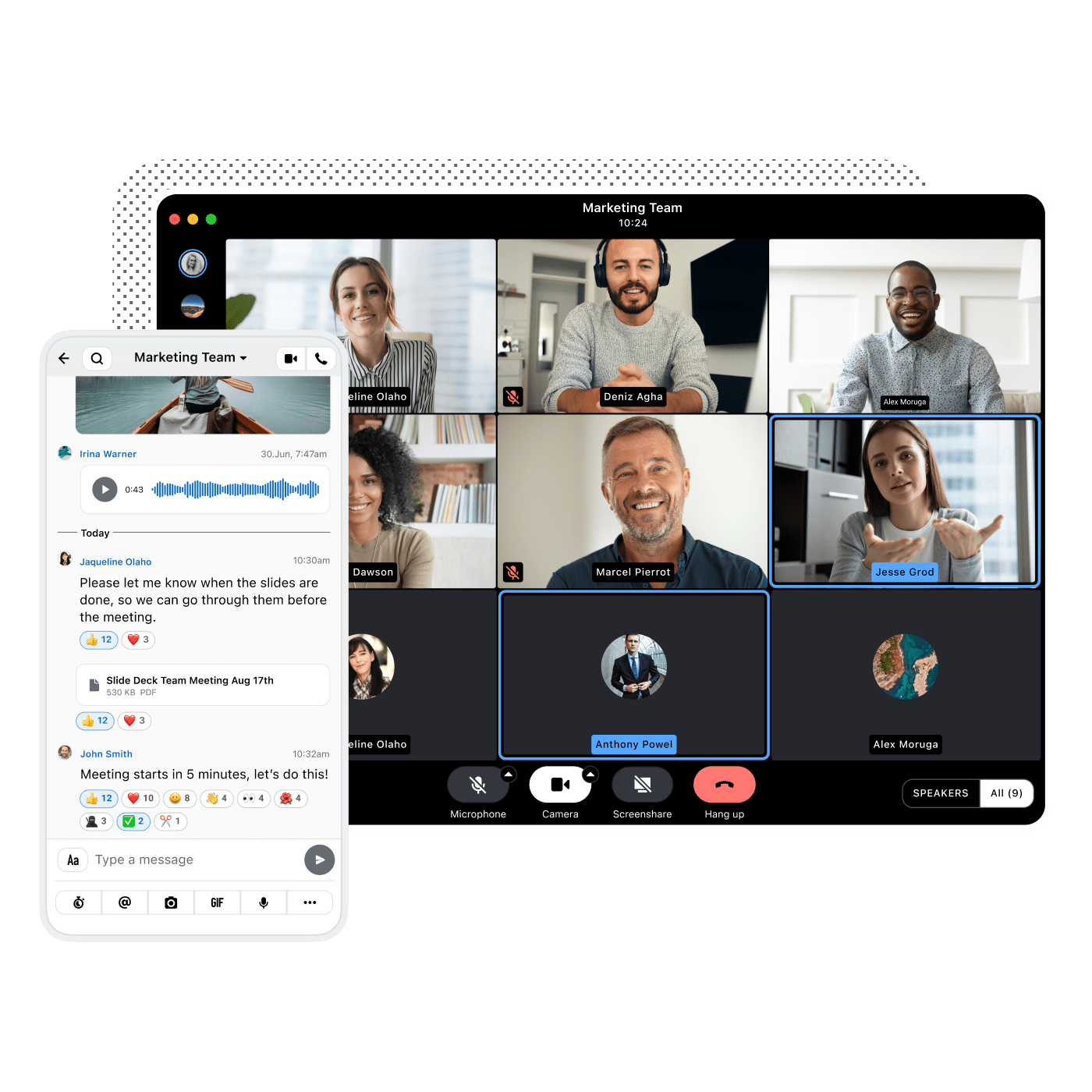

Discover key insights from Wire’s Brussels event on digital sovereignty, NIS2 compliance and secure European communication. Learn how Europe is...

Wire announces Wire Drive, integrated file management and document collaboration for Wire Messaging groups.

The BitLocker case highlights how encryption key custody and legal jurisdiction shape digital sovereignty and enterprise risk for regulated...

Wire expands its Middle East presence to support sovereign digital communication, meeting rising demand for secure, resilient infrastructure across...

Most data breaches don’t start in databases but in chats, whiteboards, and drafts. Learn why security must begin in the pre-classification layer of...

Wire reports 2X year-over-year revenue growth and expands its executive team to meet rising demand for secure, sovereign collaboration across...

Start 2026 with a fresh sound on Wire. Our new ringtone, selected by the Wire community through a global survey is rolling out across Web, iOS, and...

Wire and Collabora announce a strategic partnership to deliver secure, interoperable, and sovereign collaboration solutions under European control.

Wire and AndersenLab announce a strategic partnership to deliver secure, sovereign collaboration for European enterprises operating in highly...

Discover in a quick call how Wire enables secure, compliant, and seamless collaboration for your organization, without compromising on usability or control.