Encryption, Authority and Control: What the BitLocker Case Reveals About Enterprise Risk
The BitLocker case highlights how encryption key custody and legal jurisdiction shape digital sovereignty and enterprise risk for regulated...

The BitLocker case highlights how encryption key custody and legal jurisdiction shape digital sovereignty and enterprise risk for regulated...

Wire expands its Middle East presence to support sovereign digital communication, meeting rising demand for secure, resilient infrastructure across...

Most data breaches don’t start in databases but in chats, whiteboards, and drafts. Learn why security must begin in the pre-classification layer of...

Wire reports 2X year-over-year revenue growth and expands its executive team to meet rising demand for secure, sovereign collaboration across...

Start 2026 with a fresh sound on Wire. Our new ringtone, selected by the Wire community through a global survey is rolling out across Web, iOS, and...

Wire and Collabora announce a strategic partnership to deliver secure, interoperable, and sovereign collaboration solutions under European control.

Wire and AndersenLab announce a strategic partnership to deliver secure, sovereign collaboration for European enterprises operating in highly...

Discover how global organizations can balance innovation, compliance and data sovereignty. Technology leader Mohana Opesh shares insights on tech...

Wire introduces Chat Bubbles, a refreshed look making conversations easier to read, react, and stay in sync.

Explore the leading secure communication platforms for enterprises in 2026. Compare E2EE, metadata protection, federation, compliance readiness and...

Universal Backup lets you securely back up your Wire conversations on one device and restore them on any platform. Stay protected, switch devices...

Internal communication exposes organizations to phishing, credential theft and compliance risks. Discover practical steps to secure channels, govern...

Experience greater flexibility on Wire iOS with new multi-backend support. Securely use up to three accounts across different environments, cloud or...

Discover why secure communication has become critical infrastructure for modern organizations. Learn how to protect data, ensure resilience, and meet...

Wire and Conceptboard partner to deliver an integrated, secure and sovereign collaboration experience for European enterprises and public sector...

Learn how Messaging Layer Security (MLS) solves the scaling limits of traditional encryption and enables fast, secure collaboration for modern...

Learn how encrypted messaging apps work, why businesses need them, and which security features, like E2EE, metadata protection and MLS, really matter.

Ecosia reinvests 100% of its search profits into global reforestation while advancing Europe’s digital sovereignty. Learn how ethical tech can scale...

Explore GDPR-aligned European alternatives to Slack and Teams. Learn what features matter, from E2EE to data residency, to choose a sovereign...

A clear recap of the European Digital Sovereignty Summit 2025 in Berlin, covering France and Germany’s vision, AI and cloud ambitions, and Europe’s...

Wire and WGKD join forces to deliver secure, GDPR-compliant, and sovereign communication for church and social organizations in Germany.

Discover the best European messaging apps for secure, compliant collaboration. Learn how Wire, Threema, Element, and Proton meet EU data protection...

Explore the best European alternatives to Microsoft Teams built for security, compliance, and digital sovereignty. Learn how EU tools like Wire,...

Europe’s dependence on U.S. cloud and collaboration tools like Microsoft 365 and AWS exposes critical compliance and sovereignty risks. Learn how...

European enterprises are rethinking their reliance on U.S. tech giants like Microsoft, Google, and AWS. Discover why EU organizations need...

Discover trusted European and EU alternatives to U.S. Big Tech. Learn how enterprises can regain control through secure, compliant, and...

Discover key takeaways from Smart Country Convention 2025 in Berlin, where public sector leaders, tech innovators, and policymakers united to shape...

At this year’s Labour Party Conference in Liverpool, Wire hosted a high-level panel on Britain’s digital future, exploring how the UK and Europe can...

Wire, Europe’s leading secure communications provider, and Apostrophy, developer of the privacy-first mobile operating system AphyOS, today announced...

Wire, Europe’s leading secure communication platform, has been named “One to Watch Security – Company” at this year’s Computing Security Awards in...

The SonicWall breach highlights the tension between convenience and control. Cloud backups improve availability, but true security requires Zero...

Explore Europe’s sovereign cloud movement — key providers, adoption challenges, and how EU initiatives like Gaia-X and Virtuora drive digital...

Cloud sovereignty ensures that data, workloads, and operations stay under EU control. Learn why it matters, the key regulations, and how to achieve...
Secure communication is the foundation of digital sovereignty. See why EU organizations must harden messaging, calls, files, and metadata—and how to...

Explore how Europe’s digital sovereignty agenda is reshaping compliance, cloud strategy, and secure collaboration in 2025 and how Wire supports this...

The EU Commission ruled Microsoft 365 compliant with EU data rules. Discover what this means for enterprises, data privacy, and secure alternatives...

Microsoft’s EU Teams unbundling is more than antitrust. It’s a wake-up call for enterprises to separate sensitive from non-sovereign communications.
XWiki’s Dan Jayes explains why open source is vital for Europe’s digital sovereignty, from privacy-first tools to collective projects like OpenDesk.

Wire and agilimo deliver secure collaboration with sovereign IT operations, ensuring compliance and independence for governments and enterprises.
Discover how Meister supports public sector teams with secure, EU-based productivity tools built for easy onboarding, compliance and collaboration.

ChatControl is a flawed EU proposal for mass surveillance. Technical gaps, false positives, and inevitable evasion make it ineffective at best and a...

ChatControl threatens privacy by enabling mass surveillance of our digital living spaces. Learn why this proposal is dangerous and why protecting...

Wire is a finalist in four categories at the 2025 Computing Security Awards. Discover why Europe’s leading secure communication platform stands out...

Discover the true cost of cybersecurity breaches in 2025, from multimillion-dollar losses to regulatory fines and reputational damage. Learn how...
Discover the results of Wire’s survey of 270+ European tech and policy leaders on digital sovereignty. Learn the blockers, solutions, and steps...
Discover how Internxt is challenging Big Tech with secure, zero-knowledge cloud storage designed for privacy-conscious users in Europe.

Discover the top 5 cyberattacks on governments worldwide: what went wrong, and how secure communication can prevent similar breaches in the future.

Build a ransomware response plan with secure, out-of-band communication. Learn the 5 steps to contain threats and maintain business continuity.

Discover how Mastodon is redefining social media with decentralization, privacy, and a people-first mission. In this Wire Uncut episode, Andy Piper...

Looking for a WhatsApp alternative that meets EU standards? Discover why Wire is the top choice for secure, compliant enterprise messaging in 2025....

Explore why Wire is the best WhatsApp alternative for enterprises and EU organizations. Built for security, compliance, and digital sovereignty with...

Discover how Wire messenger keeps your messages, calls, and files private with state-of-the-art end-to-end encryption, open-source protocols, and...

Explore how data breaches uniquely impact healthcare, finance, and government. Learn how secure, out-of-band communication with Wire ensures...

When WeTransfer quietly expanded its terms of service to allow AI model training on user-uploaded files, public backlash was swift and fierce. Within...

The UK MoD data leak wasn’t just a breach, it was a failure of trust, tech, and systems. This story reveals what’s at stake when lives and public...

The CLOUD Act allows U.S. authorities to access data stored in the EU, putting it in direct conflict with GDPR. Learn how this impacts data...

Explore how Europe’s digital sovereignty is undermined by Big Tech, encryption backdoors, and chat control. Insights from Tuta’s Hanna Bozakov on...

Despite prioritizing encryption and EU data hosting, European organizations still rely on US platforms like Microsoft Teams. Explore the four key...

Despite strong regulation, only 16% of tech and policy leaders believe Europe will achieve digital sovereignty. Discover what’s holding organizations...
In a cyberattack, your primary networks may go dark. Learn why fallback communication channels are essential for crisis continuity, resilience and...

Explore how NIS2 regulations are reshaping crisis communication and why end-to-end encryption, traceability, and fallback channels are now essential...
Wire and EBCONT have joined forces to deliver secure, sovereign communication for public institutions and critical infrastructure in Europe. Learn...
Matrix talks openness but sells closed-source security. Wire exposes the contradictions in Matrix’s model and makes the case for true transparency,...
Looking for a European alternative to replace Microsoft or Google? Don't look further! Read our blog and find safe and secure solutions to 6 key...

US surveillance laws override EU privacy rules, why Microsoft and other tech giants can't keep their promises on data sovereignty, and what the EU...
Olm and Megolm expose metadata, lack forward secrecy, and fail to meet EU data protection standards. Discover why MLS is the new encryption...

Matrix's UK ties, metadata leaks, and opaque governance expose EU organizations to GDPR and Schrems II risks. Learn why Wire is the safer, compliant...
In the realm of secure messaging apps, two distinct types of “federation” exist. Knowing the difference and the implications between the two is...

Recent findings show that between September 2024 and early June 2025, Meta’s Android apps (Facebook and Instagram) covertly tracked users’ web...

Is Telegram secure or a surveillance tool in disguise? Investigative reports reveal ties to Russian intelligence and major privacy flaws. Learn what...

Wire and Scrive collaborate to improve the Haskell Servant framework, enhancing API correctness and documentation, showcasing the power of...

Discover why Wire supports strong encryption, digital sovereignty, and secure collaboration as a proud member of the Global Encryption Coalition.

Wire and Future Intelligence co-hosted a cybersecurity event at the FIFA Museum, Zurich, exploring crisis communication, resilience strategies, and...
Learn the 5 essential elements of an effective crisis communication plan in 2025. Discover how to stay NIS2 compliant, enable secure messaging, and...

Discover what WhatsApp's end-to-end encryption really protects, and what it doesn't. Learn the hidden risks to your data privacy and how metadata and...

Wire and Cloud Temple partner to offer a secure, EU-hosted platform for compliant messaging and collaboration, built for sovereignty and trust.

Learn how to build secure, compliant crisis communication plans. Explore NIS2, fallback tools, and encrypted platforms for cyber incident response.
Microsoft Teams’ optional E2EE lacks full coverage and uses outdated protocols, making it risky for compliance-driven and security-first sectors.
Eliminate login friction, simplify setup, and reduce IT stress.

A practical guide to achieving ISO 27001 certification, with key steps, common challenges, and tips for fast-moving teams seeking compliance.

Discover how ISO 27701 helps protect personal data, align with GDPR, and streamline privacy compliance in your organization.

Discover how Wire's new Global Partner Program and upcoming SDK Marketplace empower resellers, managed service partners, integrators, and developers...

Struggling with DORA compliance? Learn how to navigate legal contracts, ICT risks, and internal incident response structures for a resilient, secure...
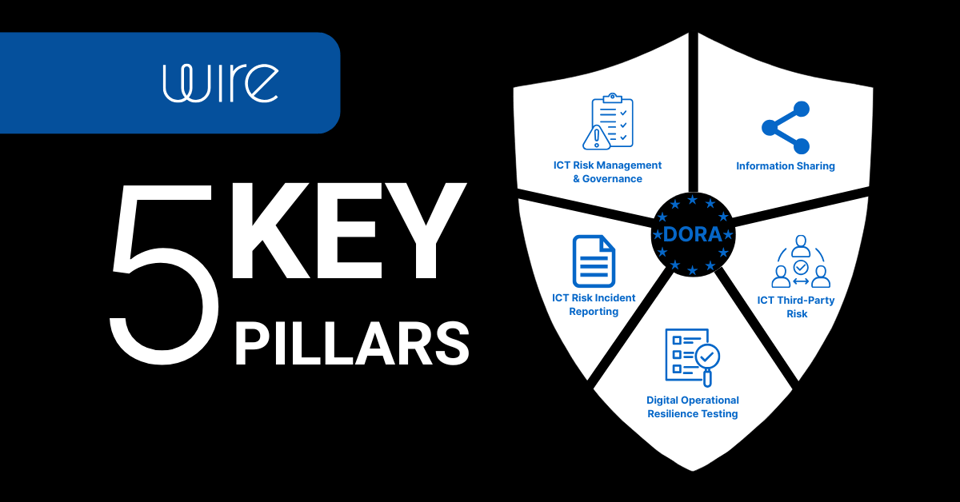
Explore the 5 core pillars of DORA and learn how financial entities can build digital resilience, ensure compliance, and secure ICT operations under...

Discover what the Digital Operational Resilience Act (DORA) means for financial services and ICT providers. Learn who must comply, and what the five...

In organizations that operate in highly regulated sectors like finance or government, there's a constant tension: how do you ensure secure internal...

Explore how ISO 27001 and ISO 27701 certifications enhance cybersecurity, strengthen privacy compliance, and boost resilience with Wire’s secure...

Wire’s Bold MLS Rollout and Navigating the Challenges of Deploying MLS at Scale

Be ready when cyber crises strike. Learn what to do in the first 72 hours after a data breach. Our checklist helps you act fast, stay compliant with...

Explore Wire’s journey to ISO 27001 & 27701 certification in this interview with our Security Director. Learn how we built a privacy-first, secure...

New Features & Enhancements to Improve Your Messaging Experience

Discover how Wire's secure communication platform supports real-time crisis response, business continuity and stakeholder trust when every second...

Discover why strong encryption matters in the digital age, and how Wire safeguards secure communication across industries amid global backdoor...

Security and compliance risks impact the entire enterprise. Learn how to align cybersecurity, regulations, and business needs in today’s complex...

A recent Signal flaw raises big questions for secure communication. Wire's SVP of Product explains how our design solves key organizational security...

Wire joins the Apple Indigo initiative as a strategic partner, advancing secure, resilient communication for defense, government, and high-assurance...

Insider threats are on the rise. Learn why internal data security is mission-critical in 2025 and how Wire helps protect your organization from the...
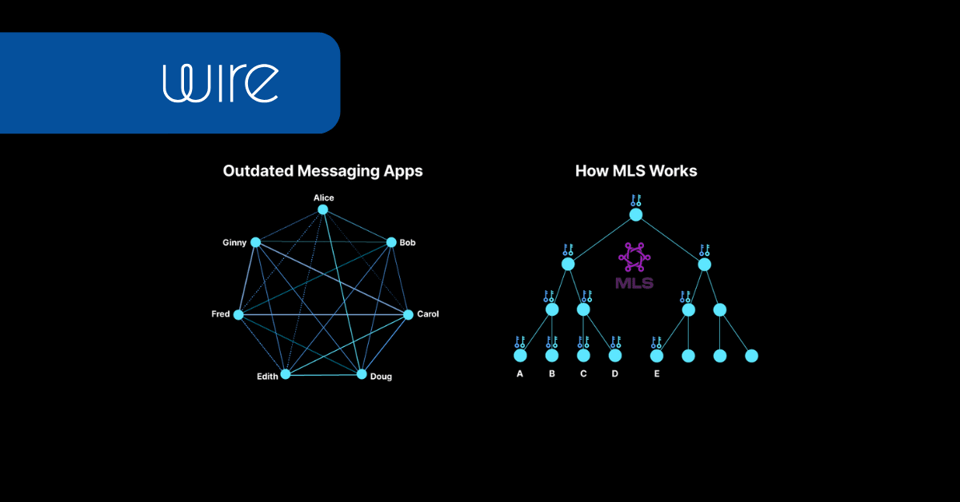
We’re incredibly excited to announce Messaging Layer Security (MLS) support across all Wire products and features.

Discover why transparent guest access is essential in secure communication. Learn how Wire’s guest and ID Shield features prevent leaks and protect...

Discover five key lessons for IT and cybersecurity leaders after SignalGate: from risks of consumer apps to why UX and admin controls matter in...

Is your team at risk of corporate espionage or data leaks on Slack? Discover how cybercriminals exploit messaging platforms and what you can do to...

In this guide we will list key factors to consider when searching for an enterprise secure messaging app, including an in-depth comparison of...

Not all collaboration platforms are secure. To help businesses choose the best secure collaboration tool, we’ve compiled five essential questions....

You don’t have to migrate to Microsoft Teams. Wire helps you to navigate through the difficult decision of finding the best alternative to Skype.

NIS2 is reshaping cybersecurity across Europe. With stricter rules and higher penalties, organizations are acting fast to meet compliance and protect...

Why is so much business communication still unencrypted? And why encryption alone is still not enough? The answer is actually pretty simple.

Opt-in security often fails to protect users. WhatsApp’s encrypted backup feature is a prime example. Discover why security should be the default,...

Stronger security and enhanced support for large enterprise communication

Discover why traditional encryption is no longer enough for critical industries. Learn how advanced security measures like Messaging Layer Security...

EU organizations face heightened data privacy risks as the EU-US Data Privacy Framework weakens. Discover why secure, end-to-end encrypted...

The Munich Security Conference 2025 explored Europe's path to strategic autonomy, digital sovereignty, and transatlantic cooperation. Discover key...

Discover how your organization can become NIS2 compliant with expert insights from Wire. Learn best practices for secure internal communication,...

What do elite motorsport racing and secure communication have in common? More than you might think.

In this blog, we focus on Wire Cells' industry-leading security approach and infrastructure.

Platform creep and app fatigue are stealing your team’s productivity, draining your budget, and creating a security nightmare. Wire Cells changes...

The reliance on consumer platforms like WhatsApp in government is a security risk we can no longer afford to ignore. Learn how attacks happen and why...

With frequent interruptions and opaque interfaces, secure workspace solutions can hinder productivity. Wire Cells will change all that.
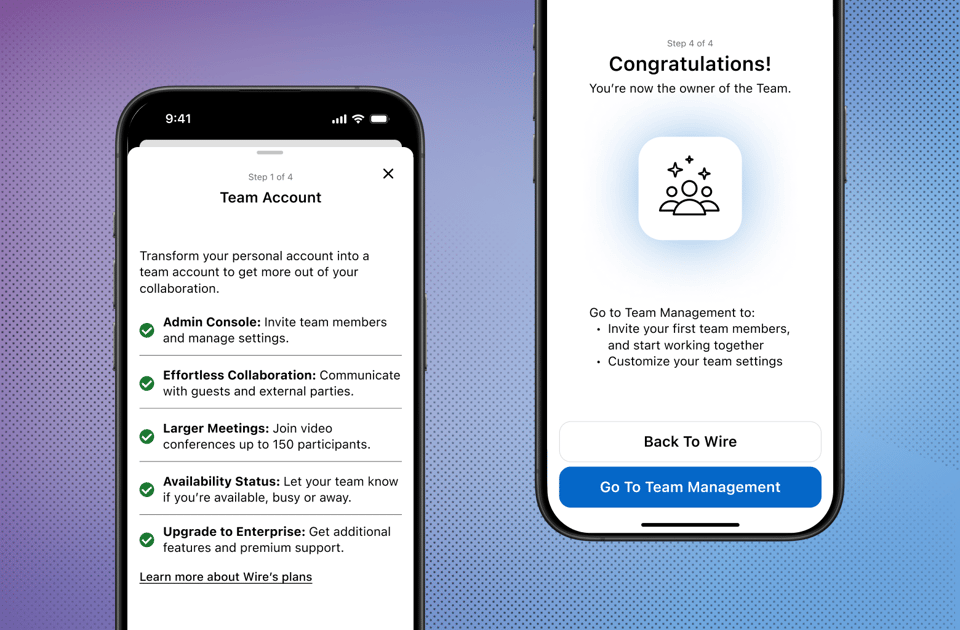
Wire introduces a seamless upgrade process from personal to Teams accounts, offering enhanced collaboration features and invisible end-to-end...

Explore the 2025 Allianz Risk Barometer insights: Cybersecurity breaches top corporate risk charts as AI elevates the stakes. Stay informed and...
Wire CEO Benjamin Schilz and Pydio founder Charles du Jeu talk about the latest acquisition and how Wire Cells will revolutionize secure...

Discover the top 7 cybersecurity trends shaping 2025, from Zero-Trust Architecture to AI-powered defenses and quantum-resistant cryptography. Stay...

Wire acquires Pydio to create the world's first fully secure workspace solution. Delivering security and productivity within a single app.

China-backed Salt Typhoon hack shows the vulnerabilities within the telecommunications industry. Learn how to easily protect your communications.

Learn why end-to-end encryption and zero-trust architecture are essential for secure enterprise communications in the wake of the China Salt Typhoon...

Scotland bans WhatsApp for official use, leading a movement towards secure, transparent government communication with platforms like Wire. Discover...

WhatsApp’s Phone Number Dependency Problem

Understand why US cloud services may compromise EU data sovereignty and privacy, and how to secure your collaboration tools.

Powerful insights and key take-aways

Your data insecurity is not a flaw, it's by design. The risks of default open federations in MS Teams and how it causes security breaches.

Learn why organizations choose Wire for secure communication and enhanced productivity in today's increasingly digital world.

Demystifying Documentation in Agile Software Projects

Avoiding unencrypted messengers or communication apps is mandatory for businesses

We need to protect privacy and data security against the EU chat control

Discover Wire's latest updates, including an improved calling UI, enhanced conversation views, read receipts, and more.

Wire and Schwarz Group announcing a strategic partnership and investment to strengthen the digital infrastructure of Europe.

New allegations show why Meta apps like WhatsApp should not be used in professional circumstances.

Wires new CEO Benjamin Schilz sits down to answer questions about his vision for Wire, lessons from companies he founded and why he is excited for...

The Taurus' leaks have shaken politics and society in Germany. We are taking a closer look on what to look for in a secure messaging solution.

Picking the right Wire deployment for your organization might be tricky. In this blogpost, we are breaking down the options to help with the decision.

Wire appoints new CEO - Benjamin Schilz | New CEO will support the international expansion of Wire.

Interview with Robert Kallwies Wires' new director for information security. Robert explains his take on security and his priorities for IT-security...

A brand new standard for end-to-end encrypted messaging, federated secure messaging and a new Android app. Only some news from Wire in 2023.

Wire joins a coalition of global industry leaders to push for open standards and innovation in technology.

Wire for Android has seen a lot of change this year. After the relaunch on a new codebase we re-introduced many features loved by our customers.

Wire removes support for Windows 7, 8, and 8.1. in future versions.

Sascha Haase, VP Product bei Wire, talks about our roadmap for secure messaging and the benefits of MLS and Federation for our customers.

Wire protects the content of our users' communication. But our commitment goes further than that - we value privacy, and that didn't change with AI.

Explore the future of secure communication with Proteus & MLS. Learn how these technologies are reshaping business messaging

The publication of MLS as RFC 9420 marks a major milestone in the history of secure communication. Find out about Wires' contribution and benefits of...

We completely overhauled our Android-App on a new technical framework. This is what is happening next.

Wire joins other messaging firms in an open letter opposing the British governments online safety bill.

Wire welcomes Juan Perea Rodríguez in Wires Senior Management Team. Before joining Wire, the digitalization expert worked for Fujitsu for many years.

Wire secures a 24m funding round to accelerate growth as a leader in secure communications.

Wire stands for security and privacy -- and we care deeply about our users. Read what we have to say about fraudulent use of our application.

Discover in a quick call how Wire enables secure, compliant, and seamless collaboration for your organization, without compromising on usability or control.